I work as a system administrator in charge of the security of the entire network and saw a great opportunity with the membership to learn more about hacking and understanding more about ways to improve our security at work. The community was helpful with up to date news, practice tests and labs that helped me. Thanks a lot for your support.
Start Your Career In Cybersecurity In Just 90 Days.
Wondering where to start to get a six-figure career in cybersecurity?
If so, you need a blueprint and step-by-step guide to get the cybersecurity career of your dreams. I’ll show you the exact plan you need to get started.

”It really made it easy for me since I couldn’t go to a traditional school by breaking concepts down into digestible bites. It’s like having your own personal mentor when you need it. That is rare in the IT Security World.”
“I also just got a position as a network administrator so there is thanks to give because of the knowledge I’ve gained” ~Marcel
My Story
The first time I tried to learn cybersecurity concepts like pentesting on my own and failed I thought that it was because I didn’t have the right skillset to learn it.
Beginner learning cybersecurity can be really hard sometimes.
Finding out where and how to get started? Even tougher.
I’ve been there. I was within the IT industry and tried to teach myself some information security concepts on my own. For years I went this route.
Yeah… that didn’t work for me.
If your strategy to learn these concepts is gathering up as much material as you can from various different sources only to find out in the end it really didn’t amount to much and didn’t push yourself further along then you’ve gone done the wrong route.
The truth of it is that it is hard to learn pentesting on your own because most of us don’t have a clue what we are doing and how to get started.
In the end if you are like me you learned a few things here and there but you are still searching for what it is you need to do next.
You need a blueprint!
Here is the blueprint…
Watch our videos
Quit trying to find bits of information from various sources like most people do and follow our proven plan that works.We’ve loaded the course within the membership with a collection of videos that really work well in teaching you what you need to know. Start with the very first one and work your way down.
Participate in our Community
Next up, join us in the community and TALK DIRECTLY WITH ME.
Follow the plan
Time to get to work! We lay out a week-by-week game plan to follow to execute the plan. Your job is to follow the plan.
What members are saying
Before this course and membership, if you wanted to learn Information Security concepts, you had two choices:
-
- 1. Spend your precious time searching down free and low-cost resources and cobbling together your own pentesting curriculum. The result? Hours spent learning bits and pieces with no clear structure… and you’re still left without the real, practical skills you need on the job, or
-
- 2. Spend $2000, $3000, or more on a high-quality classroom course and try (usually unsuccessfully) to convince your employer to help you foot the bill.
But now, there’s a third option…
Penetration Testing 101 Training Academy
LEARN WHERE TO START AND IN 90 DAYS GET YOURSELF A CAREER IN CYBERSECURITY.
You don’t have to be perfect to learn cybersecurity, pass these certifications or land an internship or junior analyst position that will get you enterprise level experience. Or the smartest person in the room. Or a type-A personality.
Six weeks from now, you can know where to start, have the fundamentals to pass any security certification with confidence and gain the skills to get that high paying Cybersecurity job.

”Being an engineer and wanting to push my career and learn more about cybersecurity is why I took the leap into this membership. For me this is one of the best e-learning platforms out there, with great content (class and labs included). I’ve highly recommended this membership to friends and colleagues.” – Jhon
-
-
- WEEK 1
- WEEK 1
Week One Accomplishments:
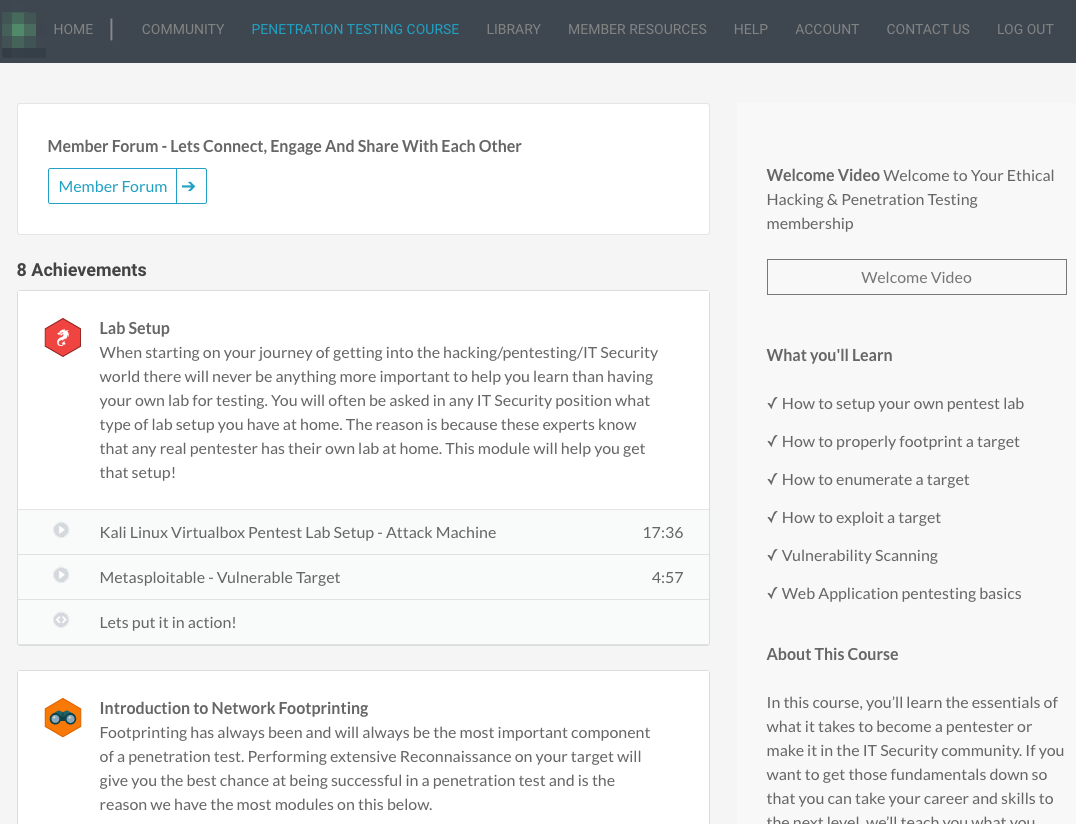
Create your own home pentesting lab setup, which is the key to learning all penetration testing concepts. We’ve found this task to be the essential difference between those who make it and those who don’t.Week One Blueprint:
Step One: We start by setting up the most important part of any pentest lab – your Attack Machine
Step Two: Now we get to the fun part of your lab – setting up your Vulnerable Target MachineCareer Benefit:
One of the first things an interviewer in the InfoSec/Pentesting world will probably ask you on an interview is what your home lab looks like. After your first week in our course you will be ready to answer all your interviewer’s lab questions. -
-
-
-
- WEEK 2
- WEEK 2
Week Two Accomplishments:
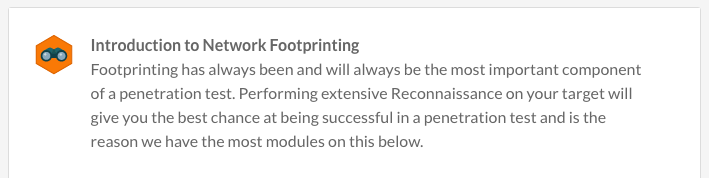
Gain the knowledge and skills that make Pentesters good at what they do – reconnaissance.Week Two Blueprint:
When it comes to Network Footprinting it is all about performing reconnaissance on your target without actually having to interact with it yet. This is the most important piece of any pentest; the better are you are at recon, the better pentester you are. Week two you will focus on how to conduct recon.Career Benefit:
Since reconnaissance is the most important piece of any pentest, you can almost guarantee a lot of interview questions regarding this but rest assured that after week two you will be ready to answer all they ask. Looking at getting your certification? This is also where many of your certification testing questions comes from as well.Course Sneak Peak:
These are just a few of the items we will cover:
• ARIN (Secret weapon to perform recon)
• Netcraft (This will make your life much simpler)
• Network Solutions (Valuable info without much effort)
• Way Back Machine (Go back in time to find what you need)
• NSLOOKUP (Your best friend during a Footprinting exercise)
• Discover Scripts (Automate much of your Footprinting)-
-
- WEEK 3
- WEEK 3
-
Week Three Accomplishments:
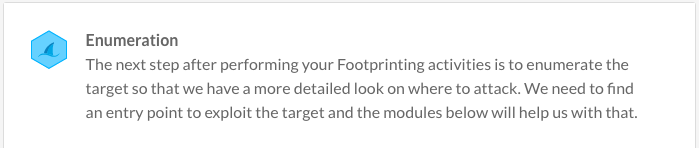
Engage any target.Week Three Blueprint:
Enumeration is taking Network Footprinting a step further where we actually start engaging the target. Enumeration goes hand-in-hand with Footprinting and this is why many of your certification and interview questions come from here as well.Career Benefit:
You will develop the crucial skills needed that will not only get you through the toughest interview questions, but have the knowledge to land a job in InfoSec!Course Sneak Peak:
These are just a few of the items we will cover:
• NMAP (One of the simplest but most powerful tools)
• Wireshark (See the attack in real-time)
• Security Camera Recon
• Maltego (Map out your target network) -
- WEEK 4
- WEEK 5
- Week 6
- BONUS: WiFi Pentesting
- BONUS: Mobile Pentesting
Week Four Accomplishments:
Exploit our targets.Week Four Blueprint:
Exploitation is the pinnacle of any pentest, the most fun and is our endgame. We gain those exploitation fundamentals and take a look at the various tactics most likely to succeed.Career Benefit:
If you can exploit it you can also defend it. Preventing exploitation is the cornerstone of any InfoSec job.Course Sneak Peak:
These are just a few of the items we will cover:
• Metasploit (The most powerful exploit tool)
• Armitage (GUI interface that uses Metasploit)
• Exploit Database (How to use the largest database of exploits)Week Five Accomplishments:
Effectively assess and scan any target.Week Five Blueprint:
Vulnerability Scanning is a must have skill in InfoSec and you learn everything you need to get the job done here.If you work in a hospital you need to continually scan your attack surface to see if you are vulnerable to prevent an attacker from stealing important patient records. If you are working for a bank you need to scan to make sure private customer information isn’t stolen. And if you are a 3rd party pentester you will also use this as a catch-all at the end to make sure you didn’t miss anything during the initial part of your pentest.By the end of week 5 you’ll know everything there is to know about vulnerability scanners and how to operate them like a pro.Career Benefit:
Whether you want to be a system admin or a penetration tester, almost all InfoSec careers have a need for vulnerability scanning.Week Six Accomplishments:
Attack web applicationsWeek Six Blueprint:
After week 6 you will have gained the skills that are most needed and sought after right now in the pentesting world which are Web Application Penetsting skills. We step right through all the popular attacks and OWASP Top 10.Career Benefit:
If you take a look at some recent pentesting job postings you will see Web Application Pentesting as one of the most sought after skills. Once you gain these skills you will become highly sought after.Course Sneak Peak:
These are just a few of the items we will cover:
• OWASP Top 10 (#1 Web App Job Application questions come from here)
• WebGoat (Premier Vulnerable Web Application)
• XSS – Cross Site Scripting
• SQL Injection
• CSRF – Cross-Site Request Forgery
• RFI Remote File Include – LFI Local File Include
• Packets
• HTTP
• OWASP Broken Web Application Project (Our Testing Platform)
• ReportingWiFi Accomplishments:
Perform a proper pentest against any target WiFi networksWiFi Blueprint:
We step right through the WiFi attacks that give the best probability of succeeding.Career Benefit:
Knowing how to properly pentest WiFi networks is a must have skill and is often done improperly. Knowing how to properly attack WiFi will give you a leg up on the competition.Course Sneak Peak:
These are just a few of the items we will cover:
• Pixie Dust WiFi Attack
• WPS Brute Force Attack
• Web Attack
• WPA2 Dictionary AttackMobile Accomplishments:
Pentest any mobile device.Career Benefit:
The world is moving mobile and those who know mobile penetration testing with be those that are most attractive to a hiring manager.Course Sneak Peak:
These are just a few of the items we will cover:
• Android Attacks
• IOS Architecture and Attacks
• Mobile Attacks put into action -
What members are saying

Taariq
I work as a system administrator in charge of the security of the entire network and saw a great...

Marcel
I purchased this membership because it seems like a great place for beginners like myself to learn...
I purchased this membership because it seems like a great place for beginners like myself to learn how to set up labs an run tests on our own without much equipment. Also the language is one that is understandable there isn’t a lot of what I like to call “jargon” its very clearly explained and that’s what I liked the most simple explanations for tasks that can be complex.
The information available on the site is easy to understand and train yourself in the ways of the ethical hacker.

Jason
Wow you guys are amazing thanks so much, ethical hacking has always been something I was interested...
Wow you guys are amazing thanks so much, ethical hacking has always been something I was interested in….thank you so very much for the lessons and knowledge to make my dreams possible
Sincerely.
FAQ
What are the benefits of joining the Membership and Community?
The Membership and Community will help you save precious time! Instead of trying to piece together a ton of different materials from different places and never accomplishing your goals we provide the exact steps you need to get where you are looking to go without all the headache.
When you join our Membership and Community, you’ll get access to all the video lessons and get access to our private community where you can discuss penetration testing and InfoSec topics with other people trying to make it in the industry just like you.
Do I get complete access to everything right away?
Yes! You get complete access to every video lesson the moment you are a member. Every lesson, every resource, every training is available as soon as you become a member.
Will there be new materials added?
Yes! New materials will be added regularly! I will be looking for your feedback to see what you would like created on a regular basis as members decide the content! We strive to create resources that will get you where you need to go.
There is so much free around the internet, why would I pay for more?
A: The membership community is for those people who want to take action, be a part of the discussion within the community forums and get full access to all the lessons and trainings. Simply, we make it much easier and quicker to get where you want to be. Ultimately, if you don’t think the price is worth investing to save some of your time and improve your career then the community might not be right for you. There’s tons of great content out there on the internet – go have a look around and we’ll always be here if you change your mind. : )
How do I cancel my membership?
A: Why the heck would you want to do that? We really hope you love the benefits of being a member so much you never cancel, but if you do decide you would like to cancel you can login to your account and then go to your Member Account Details to cancel your membership at any time.
I’m a beginner and not great with technology. Is this still for me?
When we started, we had no idea about anything infosec let along how to pentest/hack. We had to figure it all out as we went along.
We were afraid we would never be able to figure it all out. After we started, we realized our fears were only in our head.
The truth is InfoSec is not that complicated if you know exactly what to study and you have a blueprint to follow. We provide that blueprint and you will get where you need to be in no time.
A Course For Beginners
This course unlike many others is being created for the absolute beginner in mind. You will learn the basics and learn where to start so that you can build on that going forward. The biggest issue for me when starting was that there was no great resource for beginners.
A Course Based On Facts
This course was created based off of how I wish I was taught to. The information in the course is provided by experts who have studied the ins and outs of IT Security in general and hacking/pentesting to be more specific.
BONUS #1: Penetration Testing 101 Book

When you buy the membership and course you will get our Penetration Testing 101 Book as well! Download it instantly and read it when you want. This is your blueprint in written form to compliment the videos inside.
BONUS #2: WiFi Pentesting

BONUS #3: Mobile Pentesting

WHY WAIT? BUY NOW!
Why put off knowing where to start? Get the Penetration Testing101 Membership and Course right now!
-
StarterBook OnlyLet’s Get Started$29
one timewas
$53Book Only
- Penetration Testing 101 Book
- Penetration Testing 101 Course (Step by Step Videos)
- Private Member Forum
- Pentesting Practice Guides
- Regularly Scheduled Content
- CPE credits w/Certificate of Completion
- 7 Months Free
- $29 one time
-
Great SavingsBook and Monthly MembershipWant More?$39
Then $39 per monthBook plus get the course – Cancel Any Time
was
$59Save 50%Unlimited Monthly Access
- Penetration Testing 101 Book
- Penetration Testing 101 Course (Step by Step Videos)
- Private Member Forum
- Pentesting Practice Guides
- Regularly Scheduled Content
- CPE credits w/Certificate of Completion
- 7 Months Free
- $39 per month
-
Biggest SavingsBook and LIFETIME MembershipWant Even More?$299
one time onlywas
$758Save 67%LIFETIME Access
- Penetration Testing 101 Book
- Penetration Testing 101 Course (Step by Step Videos)
- Private Member Forum
- Pentesting Practice Guides
- Regularly Scheduled Content
- CPE credits w/Certificate of Completion
- Never Pay Again
- $299 ONE TIME

